By Binarly Team
The latest release of the Binarly Transparency Platform (version 3.5) introduces several new features designed to help organizations strengthen and secure software supply chains. One key enhancement is the integration and full support of YARA, the de facto standard widely used for malware detection, threat hunting, and digital forensics.
Building on this foundation, the new YARA integration connects existing threat intelligence data directly to the Binarly Transparency Platform. This enables product security, software supply chain security, and third-party risk management (TPRM) teams to scale YARA detections across product portfolios with consistency and confidence.
Some Binarly customers are already leveraging the platform for TPRM and third-party software procurement processes within enterprise environments, where these enhanced YARA capabilities provide a powerful advantage, allowing seamless integration of existing threat intelligence feeds into their analysis workflows and strengthening their overall detection and third-party risk visibility strategy.
While integrating YARA might seem straightforward on paper, simply using an open-source engine to match rules against binary files, in practice, creating, managing, and deploying YARA rules at scale is a complex and time-consuming challenge. The Binarly Transparency Platform addresses this by streamlining the entire YARA workflow through a set of purpose-built features that simplify every step of the process.
These include a YARA Rule Playground for experimentation, testing and run high-precision scans, an RBAC-compatible Rules Manager for secure and collaborative rule administration, a real-time linter that automatically detects syntax errors, and customizable metadata fields to help categorize and manage results. All of this is backed by the engineering required to scale scans across millions of files and efficiently aggregate and report detection results—delivering a YARA experience that is faster, more accurate, and built for enterprise-scale security operations.
From the very beginning, the Binarly team has been focused on advancing semantic, rule-based, and policy-driven detection technologies aimed at improving the identification and contextualization of code-level insights. Internally, we developed our first generation of semantic-focused detection technology known as FwHunt, which later evolved into VulHunt—now a cornerstone of our evidence-driven, code-based detection capabilities within the Binarly Transparency Platform.
As we continue to expand the platform, we plan to make VulHunt the primary technology for known vulnerability detection, building on what is already available to our customers and providing even more effective mechanisms to scale security operations.
While today’s announcement highlights YARA support within the platform, it’s important to note that YARA is not inherently optimized for code-driven vulnerability detection. Instead, YARA serves as a complementary capability—enhancing the platform’s flexibility by connecting existing threat intelligence and detection workflows, while technologies like VulHunt continue to power the deep semantic analysis that defines Binarly’s approach to product security and supply chain assurance.

Together, these technologies form a comprehensive detection ecosystem within the Binarly Transparency Platform. YARA provides a flexible framework for leveraging existing threat intelligence and extending detection capabilities to a wider range of binaries and software assets. In parallel, VulHunt delivers the deep semantic and evidence-based analysis required to identify known and emerging vulnerabilities at the code level. By combining these complementary layers, the Binarly Transparency Platform enables organizations to bridge traditional threat intelligence with semantic vulnerability detection, creating a unified, scalable approach to product and supply chain security.
Writing YARA rules is inherently challenging, especially when responding to threats or active security incidents. That’s why we created the YARA Playground, a complete environment for writing and testing rules. Users can develop rules interactively, test them against files uploaded to the Binarly Transparency Platform, and view results in real-time. This approach tightens the feedback loop, enabling enterprise security engineers to prototype, validate, and deploy YARA rules faster and more efficiently, before moving them into production. While this blog post focuses on YARA, the same Playground can also be used to deploy FwHunt rules, our rule format designed for firmware threat hunting and vulnerability detection.
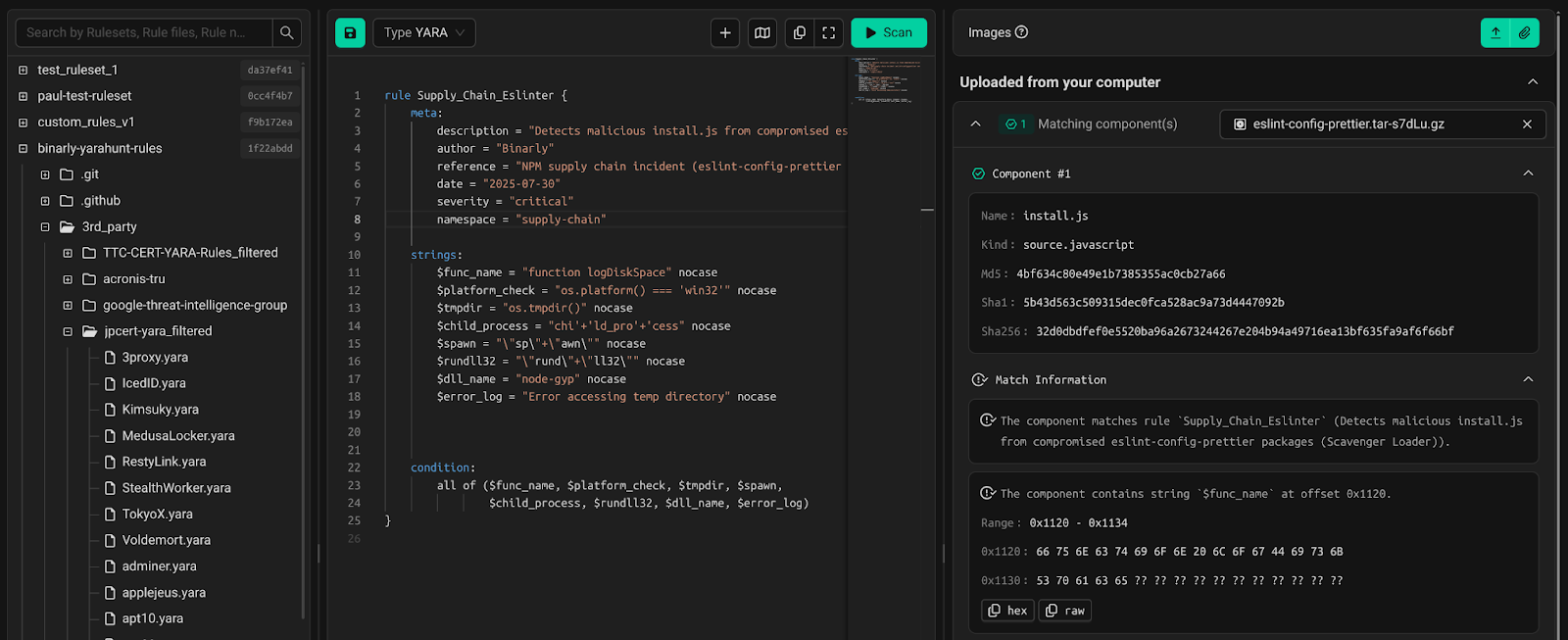
The figure above illustrates the Binarly Transparency Platform’s YARA Playground, showcasing a streamlined environment for building, organizing, and testing custom detection rules. On the left, users can browse and manage rule repositories—including internal rule sets and external threat intelligence sources. The central editor provides a dedicated workspace for writing and refining YARA rules, complete with syntax highlighting and integrated linting. On the right, users can instantly test rules against uploaded components, view detailed match information, and inspect metadata and hashes to validate results. This unified interface demonstrates how the platform transforms YARA rule development from a manual, fragmented process into a collaborative, data-driven workflow that accelerates detection engineering at scale.
The new Rules Manager functions as a centralized repository for rulesets while providing fine-grained control over access and deployment. We understand that many companies have already invested significant resources to write and curate internal YARA rules. With the new Rules Manager, these customers can upload their existing rules, re-run them, and extract more value from the effort already invested. Binarly customers can also leverage private threat intelligence feed subscriptions and seamlessly apply those rules within our platform. In fact, any set of rules can be uploaded, including those covering compliance or Third-Party Risk Management (TPRM).
Access can be managed at a granular level, which is particularly important for large enterprises where rules must remain scoped to specific parts of the organization. For example, during a security incident, access can be restricted to only the security analysts involved in remediation. From the Rules Manager interface, rule administrators can manage access and assign viewer, editor, or admin roles to specific users.
Once deployed, rule sets become an integral part of the scanning pipeline and are run automatically against products uploaded to the platform, ensuring continuous and consistent analysis across all software components.

The figure above illustrates how evidence from a triggered YARA rule is presented within the Binarly Transparency Platform. Once a rule is executed through the Playground or integrated into the scanning pipeline, the platform automatically generates a detailed evidence report. This view consolidates all relevant metadata—such as the rule identifier, author, reference, and severity—alongside matched component details and contextual indicators of malicious behavior. By surfacing these insights in a structured, easily navigable format, the platform enables analysts to trace detection logic back to the originating rule, understand the context behind each finding, and act on evidence-driven intelligence with greater precision and confidence.
The platform integrates the new YARA-X engine, a faster and safer alternative to the legacy YARA engine. Written entirely in Rust, YARA-X has been used by VirusTotal since last year. The integration in our platform was seamless, as we already use Rust for all analysis tooling.
YARA-X also improves error reporting, and we fully leverage this addition in our own custom YARA linter. The linter runs automatically and immediately flags syntax errors, usage of deprecated fields, and runtime issues that can cause slowdowns, such as slow patterns or loops with large iterations.

The figure above demonstrates the real-time YARA linter in action within the Binarly Transparency Platform Playground. As a rule is written or modified, the linter instantly analyzes the syntax and semantics of the code, identifying issues such as undeclared identifiers or invalid constructs. In this example, the system highlights an undefined variable and provides clear, contextual feedback to guide the user toward a fix. This interactive validation process helps security engineers catch errors early, reduce debugging time, and ensure that rules execute efficiently and reliably when deployed at scale.
We extended the YARA rule syntax to include custom metadata, enabling better integration of scan results within the Binarly Transparency Platform. This feature is optional and fully backward-compatible with existing rules. The first metadata field defines the severity of the rule, with levels such as Low, Medium, High, and Critical.
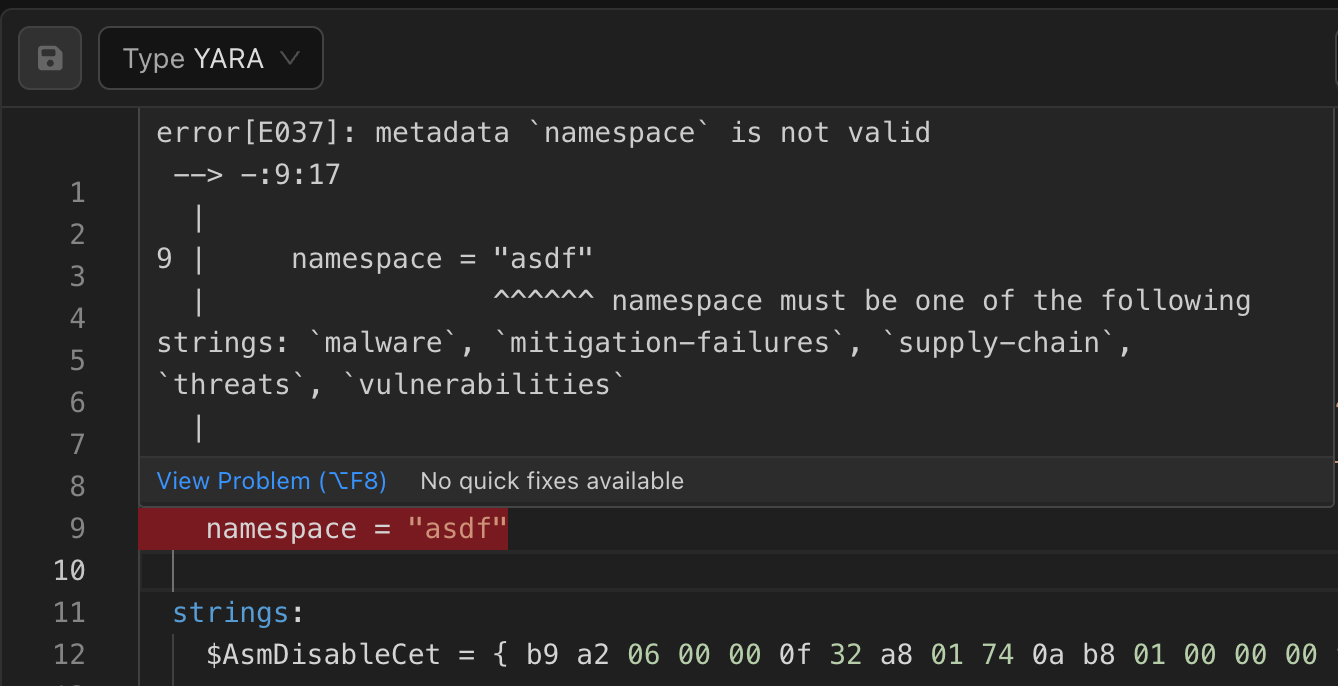
Additionally, the metadata namespace can be used to categorize rules into areas such as malware, mitigation-failures, supply-chain, threats and vulnerabilities. Our linter also supports custom metadata and reports when invalid values are used, as shown in the figure below.
At Binarly, we believe that high-quality detection starts with high-quality rules. Our curated rule sets combine precision, transparency, and continuous validation to deliver trusted results at scale.
We integrate rules from multiple third-party repositories and make them available directly in the platform. We prioritize rules that are actively maintained and enriched with metadata for reproducible detections, such as file hashes or version identifiers.
To ensure reliability and minimize false positives, each rule goes through a rigorous multi-stage validation process:
By combining automated analysis with expert oversight, we maintain a curated ruleset that evolves with the threat landscape. This helps customers detect issues faster, with greater confidence and fewer false positives.
The new YARA capabilities in the Binarly Transparency Platform represent another step toward helping enterprise organizations operationalize threat intelligence and scale product security with confidence. By combining YARA’s flexibility with Binarly’s evidence-driven approach, customers can seamlessly connect existing detection logic, streamline analysis workflows, and reduce the time from insight to action.
But this is only the beginning. As we continue to evolve our detection ecosystem, we’re preparing to open VulHunt—our semantic, code-centric detection engine—to early adopters (like Cisco Talos and Meta teams). This initiative will allow selected partners to explore advanced vulnerability detection and contextualization capabilities, directly integrated into the Transparency Platform.